Abstract: The DSP processor TMS320C6416T is used to realize IP video telephone encrypted communication based on AES block cipher algorithm and SPI bus. The hardware structure of the system is designed, the reasonable encryption algorithm and encryption method are selected, the efficient communication mechanism and data format are proposed, and the key links of software and hardware design are analyzed.
This article refers to the address: http://
At present, the speed of 100 Mbps or even Gigabit of IP networks has become possible. The increase of bandwidth provides a powerful precondition for transmitting voice and video over IP networks. IP video telephony is increasingly being widely used and will lead the trend of modern communications. However, due to the openness of IP networks, sensitive information may be easily stolen, falsified, illegally copied and transmitted, thus placing higher demands on the confidentiality and reliability of IP video communication. In order to ensure end-to-end communication security of IP video phones, SIP signaling and RTP audio and video data must be encrypted.
Skype, the world's largest IP telephony provider, has an encryption system embedded in its software. Security expert Phil Zimmermann proposed the ZRTP key agreement protocol and developed the IP telephony security software Zfone, which uses software to implement encryption when the processor performance is better. When low, this method will inevitably affect the quality of the call. To this end, a high-speed hardware encryption engine suitable for IP video telephony is designed.
IP video telephony has the following features:
(1) The occupied bandwidth is large. At present, the encoding rate of commonly used audio algorithms is about 10 Kb/s, and the encoding rate of video algorithms is about 1 Mb/s (depending on different image quality and algorithm).
(2) High real-time requirements. Human hearing is sensitive to speech signals with a delay of more than 400 ms.
(3) SIP signaling and RTP audio and video data are transmitted by UDP. UDP protocol is a non-connected protocol. Packets may be discarded if the network is busy.
In response to these characteristics, the design encryption engine assists the IP video telephone terminal to complete various data encryption functions. The key agreement and key management are handled by the IP video telephone terminal, and the two communicate through the SPI bus.
1 hardware design
1.1 processor selection
For the characteristics of IP video telephony, the processor can choose a dedicated cryptographic algorithm chip, but it lacks flexibility in use. If you need to change the cryptographic algorithm or related parameters, you need to redesign. Therefore, the system uses TI's DSP processor TMS320C6416T. The TMS320C6416T is a 32-bit fixed-point high-performance DSP processor based on the VelociTI.2TM architecture, with a clock speed of up to 1 GHz and a processing capacity of up to 8 000 MIPS [1]. It uses a very long instruction word structure (VLIW) that can execute eight instructions per clock cycle. The TMS320C6416T integrates a large-capacity memory with a two-level cache structure, namely a level 1 cache (L1) and a level 2 cache (L2).
The powerful computing and data storage capabilities of the TMS320C6416T greatly reduce the time required to implement various algorithms and cater to the real-time requirements of IP video telephony communications. It can be used for both IP video telephony terminal encryption and other high-traffic data encryption (such as streaming media servers). DSPs are more flexible and scalable than dedicated processors in dealing with changing encryption algorithms, system parameters, and communication interfaces.
1.2 Hardware Structure and Precautions
The encryption engine is based on the TMS320C6416T, including SDRAM, Flash, power supply, JTAG interface, and watchdog. The encryption engine and the IP video telephone terminal communicate through the SPI bus. The overall structure of the hardware is shown in Figure 1.
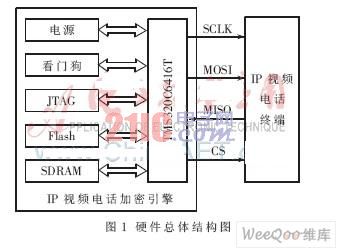
As the core of the system, DSP completes the data encryption and decryption operation, and also communicates with the IP video telephone terminal in real time, and exchanges SIP signaling, audio and video data, seed key and control commands.
The SDRAM uses HY57V283220T (4 M × 32 bit) and operates at 133 MHz for data storage. Flash uses 39VF800A (8 M × 16 bit), access speed is 70 ns, 100 000 rewritable, used for program storage and DSP power-on bootstrapping. The power supply supplies power to the entire system, the watchdog is used to monitor the normal operation of the system, and the JTAG interface is used for DSP simulation debugging.
In addition to sending pending data and commands to the encryption engine, the IP video telephony terminal also needs to have various functions such as key negotiation and management, user authority control, and network transmission. In the design process, we should pay attention to the following issues:
(1) DSP, SDRAM and other chips have large power consumption. It is necessary to set reasonable power and ground wiring width according to specific power consumption parameters, pay attention to the heat dissipation problem of the circuit board in physical space; consider DSP as BGA package, PCB should be used Multi-layer board design (8 or more layers) with separate power and ground planes to increase system reliability.
(2) The DSP works at the 1 GHz main frequency, and the SDRAM operates at the 133 MHz clock frequency. The signal integrity should be fully considered when laying out the wiring. In the actual design, the appropriate bus topology and reasonable laminated structure are adopted, and the high-speed digital signal line is added with appropriate termination to eliminate signal reflection on the basis of simulation to solve the problem of high-speed signal integrity.
2 software design
2.1 Algorithm selection and encryption
2.1.1 AES algorithm and working mode
IP video telephony has large data traffic, SIP signaling and audio and video data are transmitted by UDP, and there is inevitably a data packet loss problem. Therefore, a block cipher algorithm is suitable. Considering the speed and security of the cryptographic algorithm, the system uses AES block cipher algorithm to achieve end-to-end encryption of various data.
As an iterative block cipher algorithm, the AES algorithm can change the packet length and key length, and it is more flexible and secure in use. The argument shows that it is resistant to all known and potential password attacks at the current state of the art and is a more secure and reliable encryption algorithm. AES uses a bit stream of length 32 × Nk (Nk = 4, 6, 8) as a key, and encrypts the plaintext group of 32 × Nb (Nb = 4, 6, 8) bits each time. The length of the packet is 32×Nb bits, and the number of iterations is Nr=Max(Nb, Nk)+6.
The AES algorithm has five basic working modes: ECB, CBC, OFB, CFB, and CTR. Considering the problem of IP packet loss, if the feedback mode is adopted, the data synchronization problem needs to be considered, thereby reducing the data processing efficiency. The ECB mode is simple and easy to operate, and there is no communication synchronization problem caused by data loss. The session descriptor SDP and the audio and video data in the SIP signaling have no fixed format, and it is difficult for an attacker to analyze the ciphertext through statistical characteristics, so the ECB mode is adopted. Safe and easy.
2.1.2 Data Encryption Method
In an IP network, video and audio data are classified and segmented, and thus their encryption processing needs to be performed separately. At present, there are mainly two ways of selective encryption and full encryption for video data [4]. Selective encryption utilizes the data structure of the video data to encrypt part of the data (such as I frames) in the video stream, which helps to reduce system overhead, but the security is poor. Full encryption does not consider the video data structure and encrypts all video streams. Although the system overhead is large, the security is high. The system adopts full encryption for video, audio data and SIP signaling.
2.2 Communication mechanism and data format
2.2.1 Communication mechanism
DSP and IP video telephone terminals communicate via SPI bus. SPI is a serial synchronous communication method with communication speed of 4 Mb/s or higher, suitable for audio and video data transmission. In this system, the multi-channel buffer serial port McBSP[2] of the DSP is configured in SPI mode, the IP video telephone terminal is configured as the master device, and the DSP is configured as the slave device.
Receiving or sending data in an interrupted manner increases the burden on the CPU. The enhanced memory direct access EDMA [3] is used in combination with the McBSP, so that the CPU encryption and decryption data is performed in parallel with the EDMA data reception or transmission, which will greatly improve the operating efficiency of the DSP. The specific process is as follows: (1) The DSP receives the data to be processed through the McBSP, saves the data in the memory of the specified mapping, and then the EDMA channel carries the data to the on-chip L2 cache for the CPU to extract and process; (2) the CPU encryption and decryption process is completed. After that, it is sent to the IP video telephone terminal through the opposite path. To ensure synchronization of CPU data processing and EDMA data transmission, a pair of Ping-Pong Buffers are opened in the L2 cache for receiving and transmitting data.
2.2.2 Data format
To facilitate data interaction between processors, define the communication data format as follows:
Data header flag: 2 B in length, indicating the start of a packet.
Data type: length is 2 B, definition 0x0001 is the data to be encrypted sent by the IP video telephone terminal, 0x0010 indicates the data to be decrypted sent by the IP video telephone terminal, 0x0100 indicates the encrypted data that the DSP sends back to the IP video telephone terminal, and 0x1000 indicates the DSP. The decrypted data is sent back to the IP video telephone terminal, 0x0101 indicates the seed key transmitted by the IP video telephone terminal, and 0x1010 indicates other control data.
Data length: The length is 2 B, which indicates the number of valid bytes of data to be processed. The maximum length of an Ethernet frame is 1 500 B, so this length cannot be exceeded.
Data header checksum: The length is 2 B, preventing the head from performing a misoperation due to a transmission error.
RTP data payload: less than 1 500 B, indicating add/decrypt data, seed key, control data, etc.
2.3 Software Design Highlights
According to the DSP system architecture, considering the characteristics of AES algorithm and communication data, giving full play to the data processing capability of DSP is the focus of software design.
2.3.1 AES algorithm optimization design
The round function of AES consists of byte transform, row shift, column blending, and key plus four components [5]. (1) The byte transform is a non-linear transform, which independently transforms each byte of the state, and can be implemented by means of a substitution table (S box); (2) the row shift is a cyclic shift of each row of the state array. (3) Column mixing uses matrix multiplication on a finite field, which can be implemented by look-up table operations; (4) Key addition can be implemented by performing a 32-bit XOR operation. Through algorithm optimization, the finite field matrix multiplication and S-box can be simplified into two basic operations of table lookup and exclusive OR, and the 32-bit bus structure of DSP processor is fully utilized, which greatly reduces the complexity of the algorithm.
2.3.2 Using software pipelining technology
AES is an iterative block cipher, a total of Nr iterations, generally implemented in a C-loop program, and looping is an important factor affecting the real-time nature of the system. The software pipeline technology is used to set the operation mode of the instructions in the loop, so that multiple iterations of the loop can be executed in parallel. The program should consider a reasonable number of loop iterations to ensure that the software pipeline can proceed smoothly. Expanding the loop can increase the number of instructions executed in parallel, improving pipeline programming and improving loop performance. At the same time, the pragma indication and the compile options of -ms, -mh, etc. should be used correctly.
2.3.3 Reasonable setting of CCS compiler options
Using the const keyword to define variables can improve code performance and stability; use the -pm and -o3 options together for program-level optimization and effectively eliminate dependencies; the -mt option helps eliminate memory dependencies; these options can be greatly improved The execution speed of the code [6]. Tests have shown that choosing the C code optimization option can nearly double the execution speed of the AES algorithm.
The system key code is as follows:
Void main()
{ //Initialize CSL
CSL_init();
/ / SPI configuration
McBSP_config(&McBSPConfig);
// Ping Pong EDMA configuration
EDMA_config(hEDMAPing, &EDMAConfigRcv);
EDMA_config(hEDMAPong, &EDMAConfigSnd);
//Key expansion
KeyExpansion(CipherKey, ExpandedKey);
While(1)
{ //Encryption and decryption of data after EDMA transfer is completed
If(EDMAFlag)
DataProcessing();
}
}
3 test results
3.1 Encryption rate
Table 1 is the estimated result of the CCS software profile for each function instruction overhead.
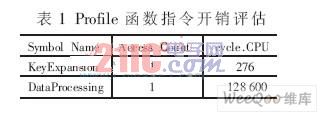
In this test, Nb = Nk = 4 and Nr = 10. After the DataProcessing operation encrypts 1 536 bytes of data, the total instruction overhead is 128,600. Taking the DSP rate of 8 000 MIPS, the running time is 128 600/8 000=16.075 μs, and the encryption operation rate is 1 536×8/16.075=765.41 Mb/s. This data throughput fully meets the real-time requirements of IP video telephony.
3.2 Efficiency comparison
References [5] implement the AES algorithm on the TMS320C54x DSP, and Table 2 gives a comparison of the two implementations.
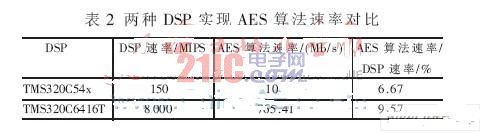
The architecture and processing speed of the two processors are different. There are different processing methods in the software design. If only the influence of the DSP rate on the algorithm rate is considered, the encryption efficiency of the system is higher. In addition, this test only considers the instruction overhead of the AES encryption algorithm code, and actually considers other tasks such as DSP access data and interrupt processing.
The system uses the DSP TMS320C6416T processor for the first time. The reasonable hardware design ensures the reliability of the system. The communication mechanism combining EDMA and McBSP improves the communication efficiency. The optimized software design improves the encryption and decryption rate. The system has been successfully applied to IP video telephony confidential communication, and can be applied to a multimedia server to realize multi-channel data encryption. This program has high reference value for VOIP, video surveillance, video conferencing and other fields.
Road Traffic Signs are graphical symbols that display traffic regulations and road information. They can make traffic regulations visually, concisely and concisely expressed. At the same time, they also express the content that is difficult to describe in words. They are used to manage traffic and indicate the direction of driving to ensure the smooth flow of roads and the safety of driving. Applicable to highways, urban roads and all special highways, with the nature of the law, vehicles, pedestrians must comply with.
Road Traffic Signs
Road Traffic Signs,Traffic Light Sign,Road Safety Signs,Highway Road Traffic Signs
Yangzhou Heli Photoelectric Co., Ltd. , http://www.heli-eee.com